Care homes are adopting technological advancements into their practices and operations and are now more connected to the wider healthcare ecosystem than ever before. While this technological revolution is welcomed, it is also increasing the vulnerability to cyber events.
Historical and current medical records, daily recordings of vital signs, treatment plans and other confidential and sensitive data, flow between hospitals, clinics and care homes, are improving the quality and efficiency of the services provided.
One emerging technology in particular, the Internet of Medical Things (IoMT), or healthcare IoT, is revolutionising the healthcare sector. IoMT applications are being utilised to improve treatments, manage diseases, reduce errors, improve patient experience, manage drugs and lower costs. This technological revolution is welcomed and is clearly here to stay. However, commensurate with the considerable positive impact of these technologies, there are emerging threats. The greater the demand for technological speed, efficiency, convenience and control, the greater the vulnerability to cyber events.
In the midst of this digital advancement, the security, safety and wellbeing of the residents, employees, and other third-parties, must be identified, understood and mitigated.
Types of cyber threats :
External threats
The types of external cyber threats are wide and diverse. Each threat is driven by a specific motive and a desired end result, with consequences as varied as the threat itself. External threats loom large and necessitate a strong cyber security stance.
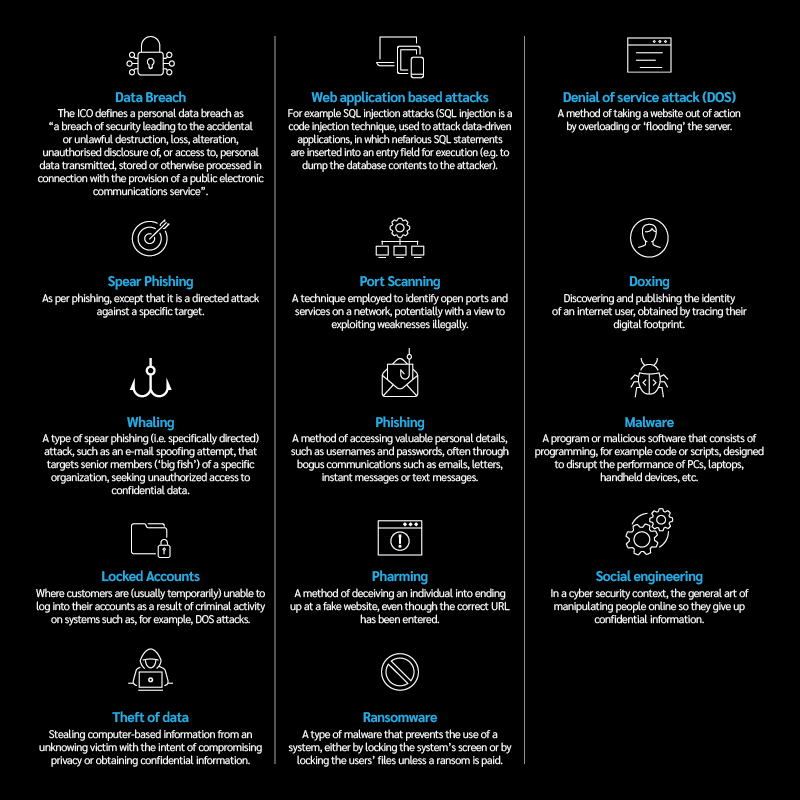
Internal threats
Despite the measures that could be taken to protect the network perimeter, no number of fire walls, multi-factor authentication methods or versions of antivirus software, will protect a business against insider threats. Cyber risks are not always external or malicious; they can and do originate internally within an organisation.
Insider threat profiles include:
Negligent insiders: human error/negligence, employees unintentionally mishandling data (either directly or through lost devices), or compromising security (e.g. phishing emails, incorporating unclean memory sticks, inappropriate use of social media/posting photos etc.)
Criminal and malicious insiders: deliberate criminal acts including mishandling of data or compromising network security for personal gain
Credential thieves: those who target insiders’ login information. Cybersecurity risks particular to care homes
Sector specific
All organisations have a cyber risk but what are the cyber risks particular to the care home sector?
Many businesses in this sector operate with modest cybersecurity budgets, limited IT support and outdated IT systems. Funds are often allocated towards operational necessities rather than cybersecurity measures and frameworks, making care homes a vulnerable target for cyber threats. Cybercriminals actively select organisations that are perceived as valuable or an easy target.
Care providers handle large volumes of personal and sensitive information relating to the residents, the residents’ family and other third-parties. Some of the information is highly regarded by cyber criminals as much of it is ‘static information’, i.e. information that cannot be changed, such as National Insurance numbers. These data command a high price on the Dark Web as they may be utilised for identity theft and other fraudulent activities.
The sharing of data with other health professionals through common online channels and platforms creates a wider threat surface. The networks may be used to gain access to larger healthcare organisations and governmental bodies, leaving the care homes vulnerable to liability claims.
Cybercriminals may manipulate, destroy or hold to ransom, electronic medical or other sensitive data. Again, this potentially leaves the care home open to liability claims, regulatory investigations and reputational damage.
The use of wearable and ambient devices, which allow carers to monitor the health, safety and wellbeing of the residents on a consistent basis (reducing the frequency of physical check-ups) is a vulnerability. If those devices are connected to a server, cybercriminals can potentially hijack the devices, and disrupt their function.
A cyber incident may cause a network outage, causing vital medical data to be inaccessible, including in the context of obtaining prescriptions.
It is crucial for all healthcare organisations, especially those which may have limited cyber resources, such as care homes, to understand thoroughly the diverse nature, impact, and origin of cyber risks, and to prepare for them effectively.
When care homes suffer a cyber-incident, the losses may be significant and varied. Unlike other sectors, where the impact of cyber events may typically include financial loss, business interruption or reputational damage, consequences in the healthcare sector may extend to the health and safety of individuals. This fact alone puts this industry in a category of risk all of its own.
Cyber risk management
Regardless of the origin of cyber exposures, implementing a robust cyber risk management framework is crucial. It is important for care homes to consider four parts of the process:
Governance
Cyber risk is not ‘just’ a technical issue but an organisational risk that threatens all aspects of care homes and needs to be dealt with at governance level, as the operational, financial and reputational consequences of a cyber-incident may be detrimental for the survival of any healthcare organisation.
To protect the organisation appropriately, the management team must ensure clear responsibility and ongoing vigilance. Despite the recent surge in cyber-attacks, and particularly ransomware assaults, research by the Institute of Directors indicates a disconnect between the IT staff, who live and breathe cyber-security and understand the consequences, and the management team.
It is vital that there is a strong alliance between the management and the organisation’s cyber risk professionals; not just communication of the relevant cyber performance figures, but also the contextual and situational awareness to bring those performance measures to life.
The cyber threat does not stand still ― it is a dynamic environment that requires constant monitoring to allow for the development of appropriate response measures.
Human factors
Human error remains the greatest cyber threat to any organisation and arguably the most underrated. Error can manifest in many ways, including:
clicking on phishing links;
inadvertent data breaches or sharing of other sensitive information;
weak passwords;
inappropriate use of public Wi-Fi; and
failing to implement software updates regularly.
Investing in cyber security awareness and education for employees is critical and dynamic, as threats change and become increasingly sophisticated.
Security
Taking account of the rapidly changing cyber space and the varying motives driving cyber attacks, care providers are urged not only to understand the nature and types of cyber risks, but also the gaps and weaknesses within their operational models that increase their exposure and appeal to cybercriminals. This might include, for example, software vulnerabilities, lack of cyber expertise, weak cybersecurity and hygiene, and dependence on IoMT.
As cyber-attacks morph and threat actors find new ways to exploit vulnerabilities and avoid detection, it is vital that care providers look very closely at their cyber hygiene protocols.
Examples of good protocols include:
multi-factor authentication for remote access (MFA);
an endpoint detection and response (EDR) solution rolled out across the IT environment;
privileged access management (PAM) and permissions across the IT environment;
secure offline backups;
an Incident Response Plan specific to ransomware that is updated and tested regularly;
a Business Continuity Plan addressing network outages, off-line communication, and data recovery protocols;
remote desk protocol access from outside the network;
updated software and patching protocols;
high-level employee awareness training;
password management software;
vulnerability assessments, including penetration testing, red-teaming and table-top exercises; and
appropriate separation of Operational Technology and Information Technology.
Partnering with a good cyber security firm will be of real benefit in the identification and mitigation of cyber threats, both internal and external, such that an organisation is well-protected from cyber threats but also adequately prepared in the event of the organisation experiencing a cyber incident.
The below chart from the National Cyber Security Centre highlights 10 steps to cyber security.

Risk transfer
An important risk mitigation process is the transfer of risk to insurance. Contrary to popular belief, property, casualty and other traditional policies are not always designed to respond to a cyber-incident. In fact, in the last several years, insurers in these areas have taken steps to specifically exclude coverage related to a cyber-attack from their policies. Specialist cyber insurance is often a better option. Although some overlaps exist, as they do with all lines of insurance, traditional insurance policies lack the depth and breadth of standalone cyber cover and will not come with experienced cyber claims and incident response capabilities. Insurers in non-cyber markets have not always fully considered the implications of cyber exposures, nor have they tackled the potential aggregation over their various types of policies.
For further information, please contact:
Andrew Nicholson , Partner, Head of Hospitality Practice
E: andrew.nicholson@lockton.com


