As published in the Australian Institute of Credit Management 2023 Risk Report.
Increased interconnectivity and interdependence of systems, brought on by digitalisation and globalisation, have created an environment where an organisation’s cyber risk maturity and vulnerability can impact debt serviceability.
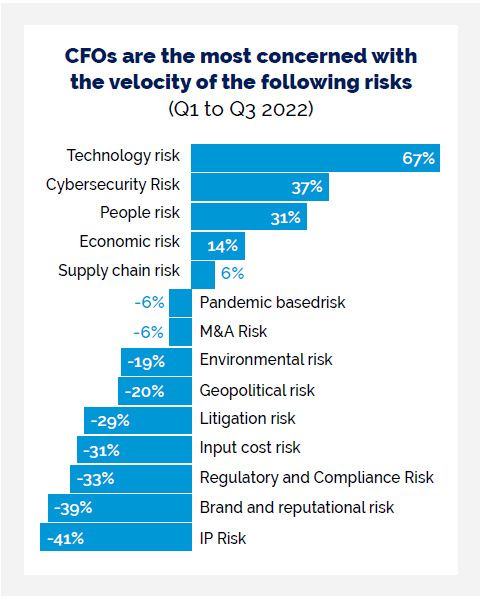
In partnership with Longitude, a Financial Times company, in Q1 and Q3 2022, Lockton surveyed (opens a new window) 475 CFOs and senior finance leaders. As the stewards of the financial health of their businesses, CFOs and finance teams including credit managers are responsible for the current approaches, and sentiments, to strategic risk management.
The CFOs’ concerns regarding risk velocity have exponentially increased particularly across technology and cybersecurity, and for good reason.
Last year, one of Australia’s largest telecoms experienced an enormous data breach with up to 10 million of their users’ personal details stolen. The hacker threatened to release 10,000 records every day unless they were paid A$1 million in cryptocurrency. The company set aside A$140 million as an exceptional expense following a massive data breach that affected 10 million customers.
Only a month later, one of Australia’s large health insurers also came under fire from a huge cyber-attack with personal data – including private health records leaked to the dark web – this was in retaliation to the company refusing to pay the ransom of A$15 million.
Medibank could face a A$1 billion compensation bill from the damaging cyberattack that has affected 10 million customers, as hackers targeting the company released the biggest tranche of sensitive data yet in another attempt to pressure it into paying a ransom.
These are both timely examples of how a cyber-attack can impact the cash flow and credit risk of a company. In 2023, credit managers must understand the impact cyber risk management can have on the cashflows of a company. It is important that credit managers start assessing the vulnerability of customers to a cyber-attack, which can have significant financial ramifications.
How can credit managers integrate cyber risks in the credit evaluation/assessment framework?
Traditionally the 5 Cs of Credit is a framework credit managers may use to help understand, measure and mitigate credit risk. The 5 Cs of Credit: character, capacity, capital, collateral, conditions. Lockton believes there should be an additional C when assessing customers: cyber risk. So, what are the top questions to ask customers?
1. How and why do you collect, use, store and delete Personal Identifiable Information (PII)?
A top risk for organisations is the re-consideration around how and why they collect, use, store and delete Personal Identifiable Information (PII). The Australian Privacy Principles (APP), specifically APP 11, already put an onus on organisations to take reasonable steps to destroy PII or ensure that it is de-identified, where it is no longer needed for its intended purpose. We can expect this to be a significant area of focus from regulators moving forward.
2. How are you mitigating cyber risk?
For example, organisations can invest in procedures to reduce the likelihood of an incident through mitigation.
Vulnerability scanning is an automated process that can help identify security flaws that could be exploited by cyber attackers aiming to take control of a business’ systems or steal its data. Weaknesses can include unpatched software or open ports. The process is purely internal facing.
Attackers will consider exploiting weaknesses in key software components in networks. The majority of successful attacks occur in systems where patches have not yet been applied. In general, it is important to have controls in place and stress test the network on a regular basis. Desktop sharing software is still the most common attack vector. Small components can create great risks.
It is therefore crucial to understand the software used in the business and using their support function to understand their ability to respond to a cyber-attack. For larger companies, phishing – essentially tricking victims to open attachments or links that contain malicious files – is a quite successful tactic.
3. How are you detecting attacks?
The average attacker will spend three months testing vulnerabilities and updates around a company’s systems. Businesses should aim to identify potential threats through device scanning, dark web monitoring and threat intelligence feeds, and remove them before they can harm the business.
Cyber threat intelligence looks at risks outside the company to understand what threats are on the horizon. It can offer insight about potential cyber-attacks and the threat actors operating at any given time. This information can be analysed and used to determine the threat level for a company and the actions needed to address the risk. Such intelligence combines information from the dark web, governments, and other third-party cyber security sources. This can be combined with cyber claims data to identify the most likely types of attacks, actors, and potential victims.
The combination of threat intelligence and vulnerability scanning can more effectively predict cyber-attacks and help prioritise the vulnerabilities to remediate, ultimately preventing losses and disruption to the business.
Many businesses are now using cloud providers to store their data and for the technology platforms they use. The downside to this is that the business loses control over the risk exposure and that it reduces a company’s options to react. If there is a big outage at a cloud provider, clients will need to rely on the service providers’ management of the situation and hope for a quick resolution. Cloud providers are unlikely to sign any liability requirements.
4. Do you have an incident response plan and scenario testing in place?
Developing a response plan and testing it regularly against different scenarios will boost the management’s confidence to be able to take the right decision in a stressful situation. These plans need to be designed carefully and need to be updated and tested on a regular basis. The management will need to rely on it for decisions such as whether the police should be called or whether ransom should be paid.
In addition, and as part of the plan, incidence response services can offer immediate technical support to a real or suspected cyber event. Such services usually include a team of forensic analysts, cyber security engineers, ransom negotiators and business resumption specialists that triage the incident. These services can help contain the threat and repair systems and get the business back online.
Good IT hygiene also requires training and educating employees. It can also involve engaging with third parties to conduct war gaming exercises or developing and testing business continuity and disaster recovery plans. A crisis management plan should include a list of experts to inform in case of an event.
5. Do you have cyber insurance?
Organisations often have contractual obligations with third parties to carry a minimum level of cyber insurance. The hardening cyber insurance market has rightfully forced a rethink on the merits of cyber insurance for organisations, however insurance is the last line of defence in a catastrophic cyber event and can directly impact debt serviceability.
Credit managers can lead the way
Finance teams are responsible for the financial health of any business. Credit managers have an evolving role to play to help build organisational resilience and ensure the organisation is protected from vulnerable customers. As the world changes and cyber risks evolve, openly discussing cyber risks and asking the right questions of customers is key when assessing credit.

