Following introduction in 2018, the EU General Data Protection Regulation (GDPR) has significantly impacted how companies collect, store and process data. Pivotal in influencing privacy regulations across the world, the legislation has received significant attention due largely to the fines that businesses could face as a result of non-compliance.
GDPR was codified into UK law as the Data Protection Act 2018 (DPA 2018). The Information Commissioner’s Office (ICO) was empowered to levy significant fines for firms in breach of regulations: up to 4% of annual turnover or GBP 17.5m, whichever is larger.
Since implementation, trends with regards to breaches and regulatory actions have emerged that are shaping the way the regulation is being applied in the UK.
Cyber incidents heavily investigated
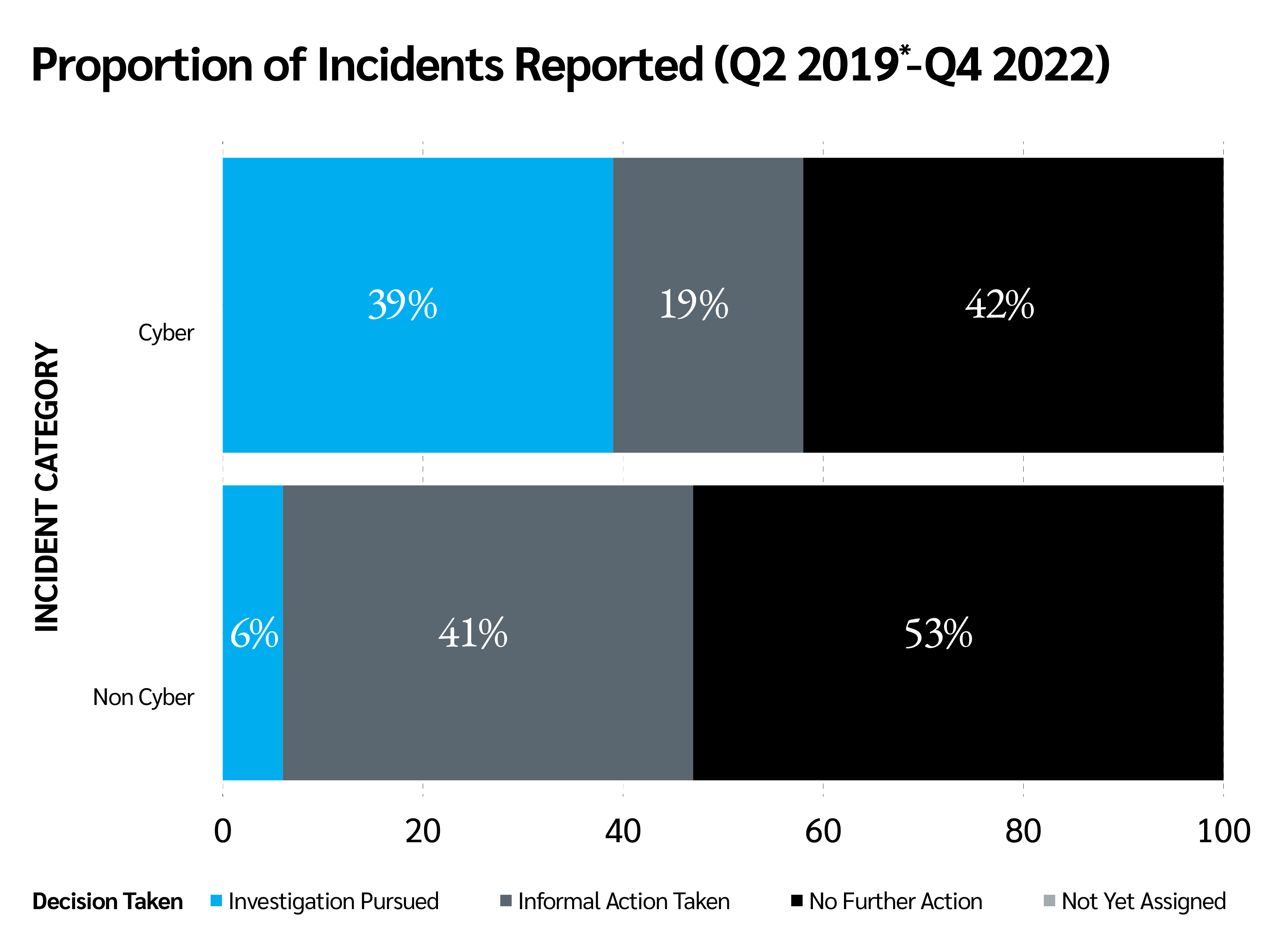
The latest published data from the ICO (opens a new window) reveals that there were 37,129 incidents of data security breaches reported between Q2 2019-Q4 2022. Of these, the vast majority of incidents (78%) were categorised as non-cyber, with cyber incidents accounting for the remainder.
However, although cyber incidents were fewer in number, they were far more likely to be investigated by the ICO. Almost two-fifths of cyber incidents reported (39%) lead to an investigation being pursued, compared to just 6% of non-cyber incidents. By contrast, the latter was more than twice as likely to be dealt with via informal action.
Source: ICO (opens a new window)
Where the ICO takes the decision to pursue an investigation, the case is passed to either its investigations or cyber investigations teams in order to determine what action, if any, is suitable in a particular case. This may not necessarily lead to a full investigation.
Ransomware the top priority
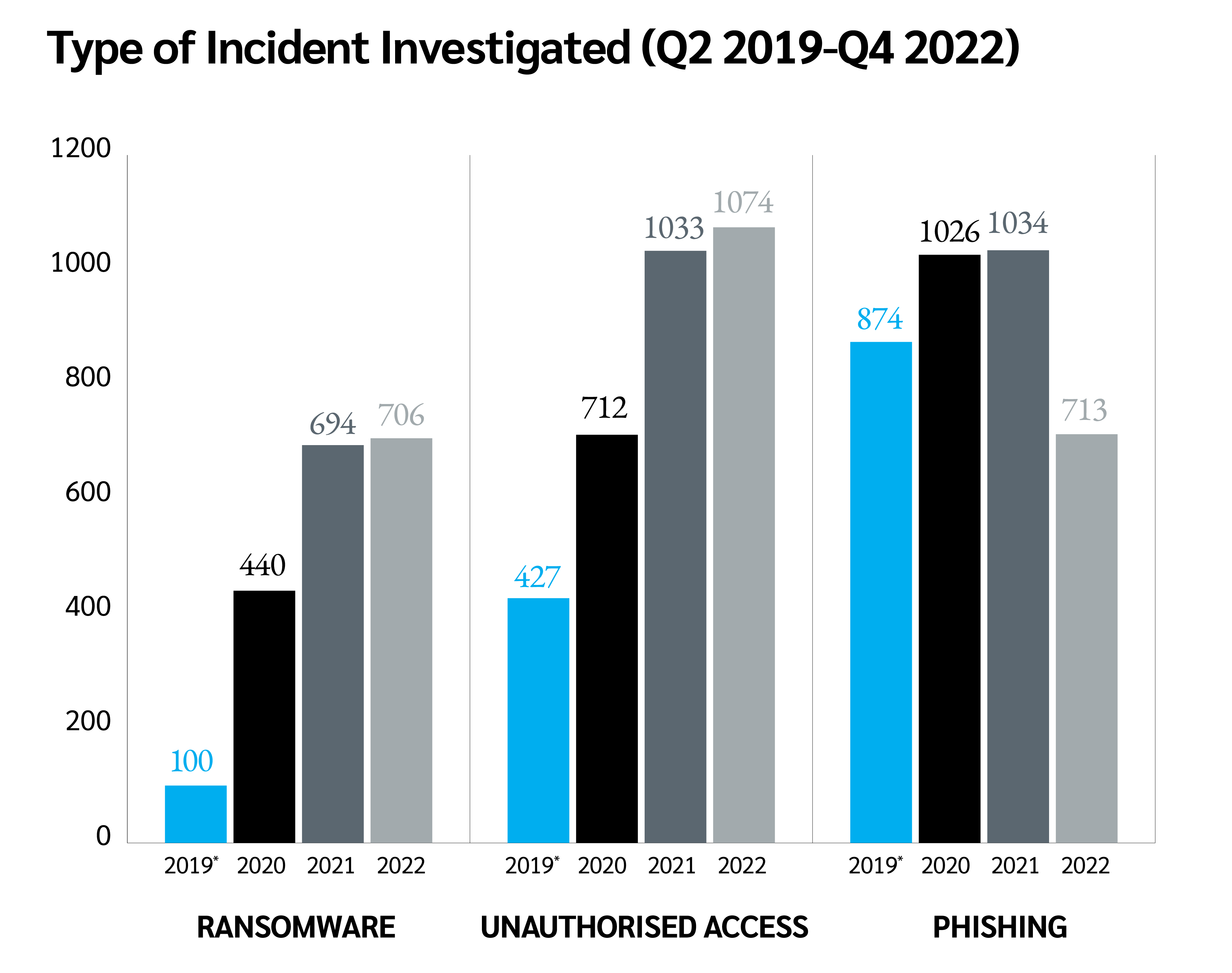
Perhaps unsurprisingly, ransomware investigations were the most common type of incident investigated between 2019-2022, accounting for almost a quarter (23%) of all investigations during the period, followed by unauthorised access incidents (20%) and phishing (11%).
Notably, these trends were heavily shaped by the impact of COVID-19, with a dramatic uptick in reports for each of these incidents in 2020 and 2021.
Source: ICO (opens a new window)
Inevitably, this increase in attacks has impacted the ICO’s ability to investigate. All ransomware attacks in 2019 and 2020 were investigated, with the figure falling to 55% and 26% in 2021 and 2022 respectively. Nevertheless, the 2022 figure remains higher than that of any other incident.
Action reserved for biggest breaches
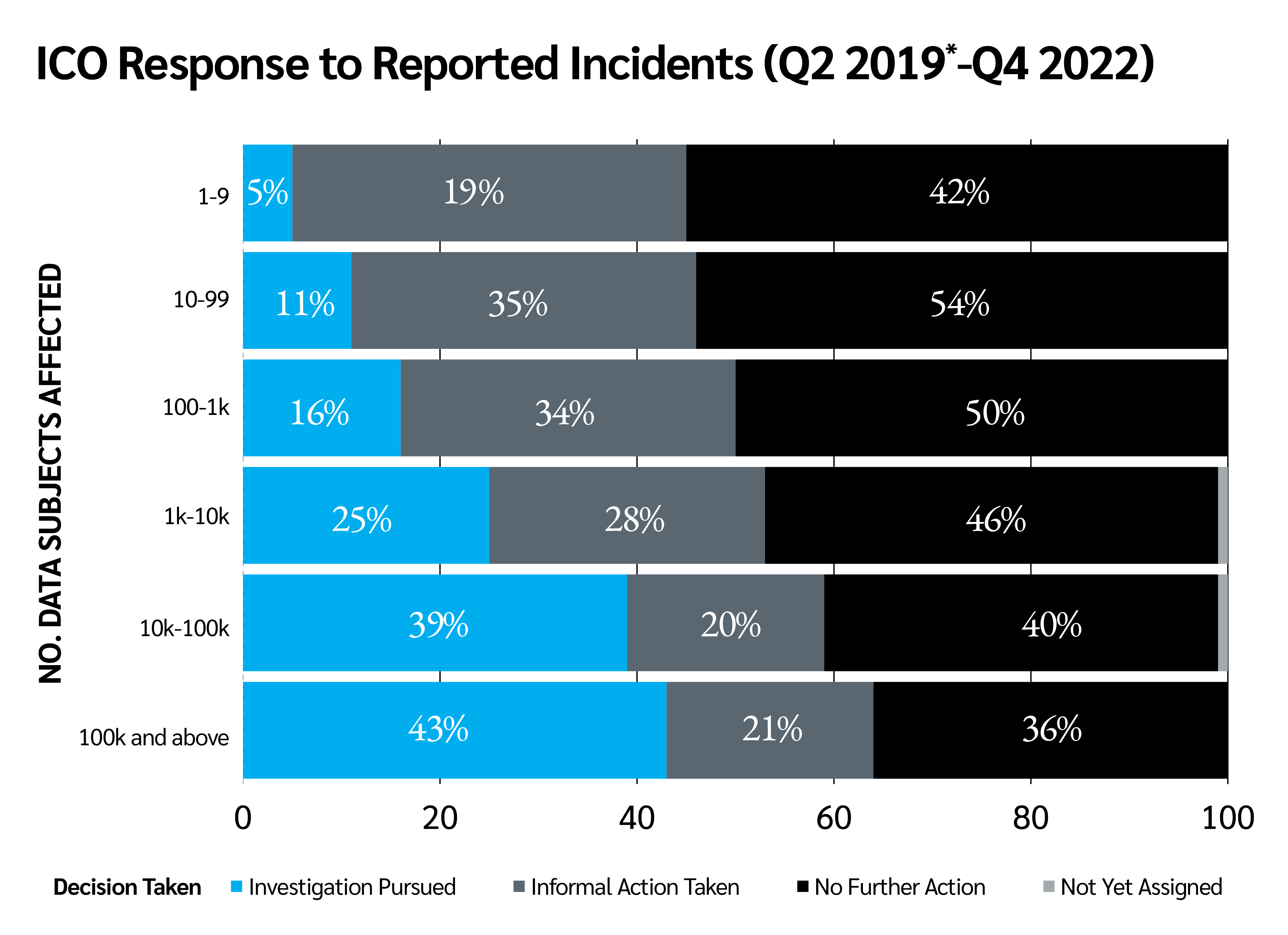
Another notable pattern to emerge among ICO investigations is an emphasis on incidents affecting the broadest number of people. Significantly, 43% of incidents affecting more than 100,000 data subjects resulted in the ICO pursuing an investigation (2019-2022), while another 21% resulted in the taking of informal action.
These figures vastly outweigh the equivalent figures for smaller data security breaches, with just 5% of incidents affecting fewer than 10 people deemed worthy of investigation.
Source: ICO (opens a new window)
Lower-than-expected fines
Against the backdrop of increasingly ‘mega’ fines (opens a new window) in the EU and US, the ICO has maintained its risk-based approach to investigation and enforcement action. Despite the fining powers given to the ICO, the UK is only responsible for the 13th and 14th largest GDPR-related fines (opens a new window) recorded so far. The regulator has noted that it must reserve the most serious sanctions for those who mishandle or misuse data.
The monetary amounts applied in these cases were far lower than originally threatened, following extensive legal action. This could be attributed to a variety of factors. The ICO voluntarily reduced these fines as a reward for the fast mitigatory action undertaken by both companies after becoming aware of the breach. In June 2019 the ICO issued a major UK airline with a notice of intent to fine it £183m (equivalent to 1.5% of the company's global turnover). However, upon review the ICO elected to reduce (opens a new window) it to £20m.
Additionally, it has been reported that the economic impact of COVID-19 is likely to have been a contributing factor to this dramatic reduction in initially proposed fines, due to the companies’ decreased revenues following the impact of the pandemic. (opens a new window) However, more recent examples such as the latest fine issued by the ICO due to the misuse of children’s data, suggest that the ICO continues to impose fines well below maximum guidelines.
On balance, firms are adhering to the rules not only due to the threat of fines, but to protect their reputation. Safety of customer data is a big asset for companies and a major component of trust in today’s world due to the introduction of the GDPR.
Recommendations
The introduction of the GDPR has increased the importance of clear documentation, processes and procedures that are managed by trained staff who engage with external experts where possible to mitigate the impact of an inevitable breach of personal data.
To provide the greatest internal security and be prepared for a potential breach of the GDPR, firms should:
Scenario test response times with incident recovery and business continuity plans
Invest in robust cyber security and staff and management training
Continually monitor incident trends and evolving best-in-class cyber-security framework
Seek external validation, audit and advice around cyber risk management processes
Consider the benefits of a cyber insurance policy to access expert responses quickly and efficiently
For more details on our products and services, please visit our Global Cyber and Technology page (opens a new window), our Management Liability page (opens a new window), or contact:
Lizzie Harris – Management Liability, Account Executive
T: +44 (0)20 7933 2442
E: lizzie.harris@uk.lockton.com
Megan Long – Cyber Broker
E: megan.long@lockton.com
This is part of a series of articles to be published on lockton.com about the GDPR’s legacy five years after its enactment. Read more about what the regulation has meant for US-based businesses (opens a new window), and look for our next instalment, which will examine the GDPR’s implications for the insurance industry.

